Gmail NOT Working, error This site uses HTTP Strict Transport Security (HSTS) to specify that Firefox only connect to it securely
You have asked Firefox to connect securely to www.gmail.com, but we can't confirm that your connection is secure.
Normally, when you try to connect securely, sites will present trusted identification to prove that you are going to the right place. However, this site's identity can't be verified. What Should I Do?
If you usually connect to this site without problems, this error could mean that someone is trying to impersonate the site, and you shouldn't continue.
This site uses HTTP Strict Transport Security (HSTS) to specify that Firefox only connect to it securely. As a result, it is not possible to add an exception for this certificate. www.gmail.com uses an invalid security certificate.
The certificate is not trusted because no issuer chain was provided.
(Error code: sec_error_unknown_issuer)
Réiteach roghnaithe
Okay, those are not the real site certificates, they are signed by a different Issuer, apparently your VPN. In order to trust your VPN as a certificate issuer, you need to import a different certificate, the signing certificate.
In IE, you would expert that certificate to CER/DER format, and then in Firefox you would import that into the Authorities tab, not the Servers tab, of the Certificate Viewer. After that, the fake JuniperSSL-signed certificates will be treated as valid.
At least, that's what is supposed to happen.
Read this answer in context 👍 4All Replies (15)
Have you had to add exceptions for any other "mainstream" sites?
Looking at your More System Details, no extensions are listed. Have you used Firefox's Refresh feature recently? This can happen when Firefox starts up slowly and says in order to make it less sluggish you can refresh/restore the browser. The best indication is that an Old Firefox Data folder appears on your desktop.
If so, your Firefox may no longer be set up to work with your security software. Some programs such as Kaspersky, ESET, avast 2015, and Bitdefender will filter your web traffic for threats. In order to filter secure sites, they must present a "fake" certificate for the site to Firefox, so they can be "in the middle" and read your secure communications. When you use the Refresh feature, then Firefox no longer is set up to trust the fake certificates.
Does that sound like a possibility?
Or if this is a new install, maybe Firefox needs to be set up for the first time to work with one of those programs.
Also, if you don't have the Flash plugin for Firefox, you can download it here: https://get.adobe.com/flashplayer/ (make sure to uncheck any unwanted extras)
Or get the plugin based Flash player from https://www.adobe.com/products/flashplayer/distribution3.html as you will only get Flash.
Open this chrome URI by pasting or typing this URI in the location/address bar to open the "Add Security Exception" window and check the certificate:
- chrome://pippki/content/exceptionDialog.xul
In the location field type/paste the URL of the website
- retrieve the certificate via the "Get certificate" button
- inspect the certificate via the "View..." button
Hi Friends, Thanks for reply, none of them solves my issue. Also I have one simple question, Gmail works fine in IE and Chrome but not in Firefox, this purely means my security application (antivirus etc) are not playing any role in the error displayed. This looks like some issue in Firefox only....
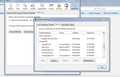
Attached screenshot of error
Firefox has a separate certificate store from IE (Chrome uses IE's certificate store), so yes, there is an extra setup step. Are you planning to research that on your own? If you want suggestions, it would help to mention which security application it is.
Please do mention if this really solves the problem, just for information, i have already loaded gmail and mail.google.com certificate into firefox but issue persist
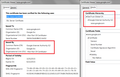
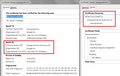
Screen shot attached of certificates imported in Firefox
Where did you import those server certificates from? You should never need to make individual server exceptions for mainstream websites like google.com.
If you view one of those certificates, what do you see in the "Issued by" section? We want to help determine whether they indicate a configuration issue with your security software or malware.
A Google search suggests that these are certificates from a VPN (Juniper SSL). The usual way to proceed is to install a root certificate and set the trust bit(s) to allow the certificate to behave as a trusted root certificate. You can check out the certificate chain in other browsers and export the root certificate of that VPN if there is none and import this certificate in the Firefox Certificate Manager. Remove all the exceptions that you have so far.
Since i was getting exception in Firefox while loading gmail.com, i exported gmail certificates from IE and then imported in firefox as image shared earlier. But this too dint helped much. Need to get this resolved else no use of firefox in system and would uninstall it
Réiteach Roghnaithe
Okay, those are not the real site certificates, they are signed by a different Issuer, apparently your VPN. In order to trust your VPN as a certificate issuer, you need to import a different certificate, the signing certificate.
In IE, you would expert that certificate to CER/DER format, and then in Firefox you would import that into the Authorities tab, not the Servers tab, of the Certificate Viewer. After that, the fake JuniperSSL-signed certificates will be treated as valid.
At least, that's what is supposed to happen.
Thanks imported in Authorities tab (Juniper SSL) and now its working...Why this issue is only in Firefox ...knowing gmail is well used email app, this should be included in basics of Firefox
Hi malaniom, Mozilla has always used a certificate store separate from the one maintained by the OS. Google decided to use the local one with Chrome, so software designed to insert authority certificates into the Windows certificate store allows both IE and Chrome to work seamlessly with fake certificates signed using that signing certificate. Of course, we've seen cases where this is exploited by malware, and the malware comes to light because Firefox still rejects the fake certificates. So sometimes the separate certificate store is for the best and other times it's a PITA.