templates on Win 2012r2 not working
I've applied the admx templates to the Sysvol on our Win Server 2012r2 environment & I've created a GPO to allow NTLM authentication to our intranet sites. However when I deploy the GPO I do not see the site in about:config network.automatic-ntlm-auth.trusted-uris
using gpresult /r I can see that the GPO is getting applied on our test machine.
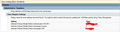
attached is an image (first image) of the Firefox templates when added to the domain controller (Win 2012r2) -
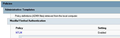
I tried on another test Domain controller (this time Win 2016) and noticed that the templates look different. When applied to the Win2012r2 DC they seem to have been placed under 'Extra Registry Settings' (see first image) however when I placed them on my 2016 box, they were assigned to a different category (see second image).
Ñemoĩporã poravopyre
Are you using ESR or rapid release? Do other policies work?
The NTLM policies were accidentally marked enterprise only. I'll be fixing that.
Emoñe’ẽ ko mbohavái ejeregua reheve 👍 1Opaite Mbohovái (4)
EDIT: I checked on the Win 10 Pro device (included on the GPO) and it has applied the GPO (gpresult /h c:\temp\gp.html ) for Firefox, however when I go into Firefox and about:config I still dont see the trusted-uris.
Ñemoĩporã poravopyre
Are you using ESR or rapid release? Do other policies work?
The NTLM policies were accidentally marked enterprise only. I'll be fixing that.
mkaply said
Are you using ESR or rapid release? Do other policies work? The NTLM policies were accidentally marked enterprise only. I'll be fixing that.
all other policies are working (there's a policy for IE to apply trusted intranet, which works fine).
Your question about if I was using ESR might be onto something. I've got ESR 60.0.1 (which is the working GPO) on my test rig, and standard 60.0.1 on my other (non working test rig).
EDIT: you cracked it! in order for the GPO to work successfully, you must be using ESR 60.0.1 - which is incredibly strange as the standard (non ESR) version was also 60.0.1 but didn't work. My understanding was the ESR was only different in the frequency of updates & not fundamentally different than standard?
We've documented the differences here:
https://support.mozilla.org/en-US/kb/choosing-firefox-update-channel
We're on figuring out how to make them closer.
I'm also going to be updating the templates to make it more clear that some policies don't work on rapid release.