All websites trigger security risk
I have added exceptions, I have gone through About:Config. Every website I need to use for work including how I clock in to just trying to use Google for either a search or to access work email gives the SEC_ERROR_CA_CERT_INVALID. Every single site I go to - including trying to access Mozilla support. Every site has been added as an exception and it still gives me the security error.
I work between two computers right now and my old one with the same version of Firefox does not do this. No exceptions, no messing with About:Config - it goes to the sites with no problems. The network I use does not have anti-virus and there is no anti-virus on the two Macs I use.
I know it isn't the websites either as Chrome and Safari both load what I need with no problems either. And this is recent as when I set the new computer up just this past Monday, 12/16/2019, everything was working fine and Firefox was syncing from the old computer and loading all sites fine.
所有回覆 (17)
Hmm, possibly the certificate store file has become corrupted. Could you try the steps in this article, in the "Corrupted certificate store" section toward the end: What do the security warning codes mean?
You can also check the date and time and time zone in the clock on your computer in case your current internet time server is off.
jscher2000 said
Hmm, possibly the certificate store file has become corrupted. Could you try the steps in this article, in the "Corrupted certificate store" section toward the end: What do the security warning codes mean?
Followed that and nothing, I still get the warning. I've been through most of the Mac's Library folder going to the areas that should have Firefox folders and am finding nothing that could cause it.
cor-el said
You can also check the date and time and time zone in the clock on your computer in case your current internet time server is off.
Time zone is set automatically with location and is correct, as is the date.
由 EDAnderson 於
Do you get the error page with the Advanced button that provides access to more information? If so, the error code in that section may work as a link to show a coded version of the certificate, or there might be a View Certificate button. That could help figure out whether the problem is caused by a "man in the middle."
You could test this alternative configuration, which would switch Firefox from using its own certificate store to using the Mac system keychain to verify website certificates:
(1) In a new tab, type or paste about:config in the address bar and press Enter/Return. Click the button accepting the risk.
(2) In the search box above the list, type or paste enterp and pause while the list is filtered
(3) Double-click the security.enterprise_roots.enabled preference to switch the value from false to true
jscher2000 said
Do you get the error page with the Advanced button that provides access to more information? If so, the error code in that section may work as a link to show a coded version of the certificate, or there might be a View Certificate button. That could help figure out whether the problem is caused by a "man in the middle."
You could test this alternative configuration, which would switch Firefox from using its own certificate store to using the Mac system keychain to verify website certificates:
(1) In a new tab, type or paste about:config in the address bar and press Enter/Return. Click the button accepting the risk.
(2) In the search box above the list, type or paste enterp and pause while the list is filtered
(3) Double-click the security.enterprise_roots.enabled preference to switch the value from false to true
The values are already set to "True".
Hmm, can you try switching it back to the default setting of false and see whether that works? If it won't change, that can indicate it was locked by an external settings file.
That's a no-go too.
I double checked updates - to be on the safe side - and all the possible updates I can do are done for the software and MacOS.
EDAnderson said
That's a no-go too.
You can't change it, or same error? You might need to restart Firefox after changing the setting (and then make sure it stayed changed).
It gives me the same error after changing and restarting Firefox.
I would love to see the details on the invalid certificate. Unfortunately, there are two error pages and only one of them has the Advanced button. Can you find that button to obtain details on the certificate, either from a View Certificate button or by clicking the error code?
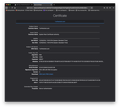
When I click on the error: https://www.ontheclock.com/time-clock/
Issuer certificate is invalid.
HTTP Strict Transport Security: false HTTP Public Key Pinning: false
Certificate chain:
BEGIN CERTIFICATE-----
MIIC/TCCAeWgAwIBAgIILE/GgMCg7CswDQYJKoZIhvcNAQELBQAwLDEqMCgGA1UE AwwhU3lzdGVtIFJvb3QgQ2VydGlmaWNhdGUgQXV0aG9yaXR5MB4XDTE4MTIxOTE4 MTkxNloXDTI0MTIxODE4MTkxNlowGzEZMBcGA1UEAwwQKi5vbnRoZWNsb2NrLmNv bTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAJeMgd5EOLnheUj+JM54 mo33H0SN/QdwEtBtV5MufrxJyH/RxfXp6s88GCRMbGt8Hz2uuM8h2huBCxpyWwHL 6dmGGLhb8/PtcxjkBRypKzWnxxmFie9uWRd92LPWOd1fl4ZYBUYBQ3nVRRNhdOWS tQIcYCEZc7tvkLedZ9DjsT4DF4nZqr+ovvGB5GgMjPZEhHCw0TFlUJuk+V2GmePB y1rTNGgSg0S5trus/FRcG7FwpJkEqrLLklFnnqnhGNyz8ggDsYYonzRqhMs//Sdv 6KCflyN+v4JmMtaMdWb4PrACraHuAFzDdDFsZ5u+t9iUmakF7+aQD715D0uyqlYS hqkCAwEAAaM0MDIwGwYDVR0RBBQwEoIQKi5vbnRoZWNsb2NrLmNvbTATBgNVHSUE DDAKBggrBgEFBQcDATANBgkqhkiG9w0BAQsFAAOCAQEAFqUV9N7laNFGY25g+Eza Oz/VTFF2J1/PyUMVpj0mBwXiUNBeB+744ZxDtf7t99Mv3bzYirayY6R1uNU01SxO UyTjKGOpTKRFvaxpikZ608BZVDjfku2b0Bus1nXWbPSxWUMfY55yYtHe0s6V5xzq zSa9vt9SOiAV41cIS7wn9bX3zEQaNDjJV5IzNxwZK1Sc6KJGppNsi8D+K3/Oayxj r+5E+NIt4u0HFoIOiUgHiPHFcyW75oSkzlxhhjB+RnqFGtTxo7q9HH+5w5jwsxoB fAsC5M+bHmFwwIHPTiRdONtitnsDVpbrV41fNQXamEA7DY3KXT5JYOdsUyMddqrw eg==
END CERTIFICATE-----
Screenshot is from clicking on view certificate.
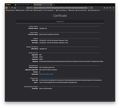
Accessing google for email and the like doesn't give an advance button, but here's the info for that too:
Issuer certificate is invalid.
HTTP Strict Transport Security: false HTTP Public Key Pinning: true
Certificate chain:
BEGIN CERTIFICATE-----
MIIC9TCCAd2gAwIBAgIIHf9NmyrZ95MwDQYJKoZIhvcNAQELBQAwLDEqMCgGA1UE AwwhU3lzdGVtIFJvb3QgQ2VydGlmaWNhdGUgQXV0aG9yaXR5MB4XDTE4MTIxOTE4 MjIyNVoXDTI0MTIxODE4MjIyNVowFzEVMBMGA1UEAwwMKi5nb29nbGUuY29tMIIB IjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA0mNj6tWArJqrMwoLFhT4Ps8z vk4SQlH1qV1xo5SPrPa5g4xizqEnLg/whAguyA5ZwArjzqG+/JCWcvp//e5gtAtU merwRZafe0LLue5qH0ZG65UGCnqIOIwgzn5TF9dEcjBXR/ZFp6jM2NWwapgpBOEF WjpG3iKey6rFgfyzJOxBhQC4/ywqXKJqcNwzP6DVuqO3UU8+eKVMiDHIIgPLeu+e 0z7ZzvaDT61RGAhL2zba3dML9Iq82o1nCHlqsJxN2OvPfayPuzwiXowPTSKB7DGA a/JXvCnkZtb4n0aUdvV3t5WsJtPBF170kGq5g5m6WnJD1nDTI0AU6ibqmw46vwID AQABozAwLjAXBgNVHREEEDAOggwqLmdvb2dsZS5jb20wEwYDVR0lBAwwCgYIKwYB BQUHAwEwDQYJKoZIhvcNAQELBQADggEBACoDjnhNYN8t4wk+b48X3vbuGNK4FgKo Qu6QLBcBAtF4y10+B7PCiS6oLNFqxcW++bmtVylBA2Nr+4wzX84Q5M88tKY0fdDd IN/hPIyIs52N2WwNN93x6SgzMEGO4iCO7uZeAEAc6D9BPbS7EWIN+uLHe/r8Atoi tMyGsUG4Vfl9ZZQYJc+bvA1uYyX/E16lSSeqrGbWwKRl2JJjdeGsBREO4iAsFS5z IDKUgm51PTlFSSBZpN1x+wzc947LFD30r6Dl/6O57bfRvvdB3W8SEhE904UHvJyM vuHNPp7cfkRJjKUhbD+tg/U1MdvnIz5jow1nxt2cnXLBZ0PVjkoavNQ=
END CERTIFICATE-----
Hmm, "System Root Certificate Authority" sounds totally fake. The certificate issue dates are interesting:
(1) ontheclock: 19 Dec 2018, 6:19 p.m. (2) google: 19 Dec 2018, 6:22 p.m.
Are these times linked to when you visited the site, maybe the certificates are being faked up in real time?
I think we have to approach your system as though it is infected/hijacked, but I don't know the culprit. You could start with Malwarebytes (free trial, no payment needed). However, I suggest downloading it on a trusted system in case your requests may be intercepted and sent to malicious servers.
https://www.malwarebytes.com/mac/
You might also want to go straight to the specialized forums listed in this support article where they can guide you on using advanced tools: Troubleshoot Firefox issues caused by malware.
One other thought: what if you enable DNS over HTTPS to try to bypass any modified DNS settings? Try:
(1) In a new tab, type or paste about:config in the address bar and press Enter/Return. Click the button accepting the risk.
(2) In the search box above the list, type or paste TRR and pause while the list is filtered
(3) Double-click the network.trr.bootstrapAddress preference to open an editing field, type or paste 1.1.1.1, and press Return to complete the edit or click the blue check mark button
(4) Double-click the network.trr.mode preference to open an editing field and change 0 to 3 (which means only use DoH, never fall back to MacOS doing your DNS lookup) and press Return to complete the edit or click the blue check mark button
If that doesn't make any difference, you can restore normal DNS using the reset button at the end of each of those two rows.
Note: because DNS responses are cached, test using a secure site you haven't visited recently, for example, you could try the Malwarebytes link above or https://duckduckgo.com/.
"The poxy server is refusing connections"
Hmm, is your Mac set up to use a proxy server?
Not so far as I know. I've been able to locate a backup of my old computer and am running that now. We'll see what happens.
The system install from the back up seems to have worked. I'll know for certain when I come into work on Monday.