CORS request did not succeed
To whom it may concern,
I have an angular application accessing data from a 3rd party data provider. To get data, POST-requests are sent to the data provider REST API (https://capzlog.aero). The application works correctly using Google Chrome and Microsoft Edge. However, when using Firefox, the following error appears:
"Cross-Origin Request Blocked: The Same Origin Policy disallows reading the remote resource at https://capzlog.aero/api/pel/public/externalsystemflights/GetMissingIDs. (Reason: CORS request did not succeed). Status code: (null)."
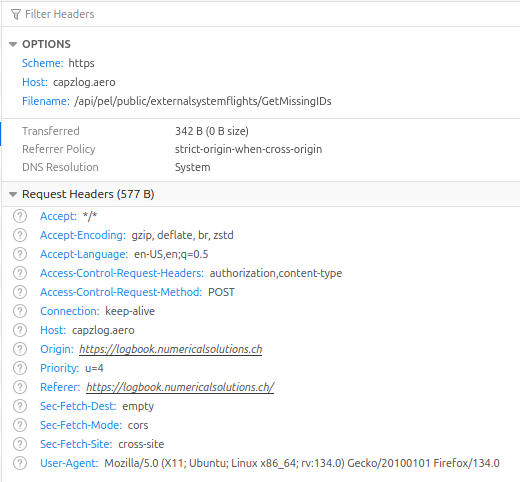
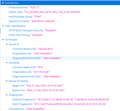
As the POST request contains basic authentication, a preflight-request (OPTIONS) is first sent to the data provider. This request fails when using Firefox (but not when using Chrome or Edge), see attached screen-shots.
I have spent 4 days on the internet trying to figure out a solution, but I could not solve the issue. I tried the following: 1) check the certificates of the 3rd party provider (https://capzlog.aero): There are no issues. 2) start Firefox in safe-mode, disactivating the "Enhanced Tracking Protecting", clearing the cache. 3) changing the following Firefox settings:
security.enterprise_roots.enabled (true<->false) security.tls.version.min (1<->3) security.tls.version.max (2<->4) network.http.network-changed.timeout
I tried sending the "OPTIONS"-request using curl and it worked as expected:
curl --verbose -XOPTIONS -H "Access-Control-Request-Method: POST" -H "Origin: https://projectz.numericalsolutions.ch" https://capzlog.aero/api/pel/public/externalsystemflights/GetMissingIDs
- Host capzlog.aero:443 was resolved.
- IPv6: (none)
- IPv4: 156.67.9.80
- Trying 156.67.9.80:443...
- Connected to capzlog.aero (156.67.9.80) port 443
- ALPN: curl offers h2,http/1.1
- TLSv1.3 (OUT), TLS handshake, Client hello (1):
- TLSv1.3 (IN), TLS handshake, Server hello (2):
- TLSv1.2 (IN), TLS handshake, Certificate (11):
- TLSv1.2 (IN), TLS handshake, Server key exchange (12):
- TLSv1.2 (IN), TLS handshake, Server finished (14):
- TLSv1.2 (OUT), TLS handshake, Client key exchange (16):
- TLSv1.2 (OUT), TLS change cipher, Change cipher spec (1):
- TLSv1.2 (OUT), TLS handshake, Finished (20):
- TLSv1.2 (IN), TLS handshake, Finished (20):
- SSL connection using TLSv1.2 / ECDHE-RSA-AES256-GCM-SHA384 / secp384r1 / rsaEncryption
- ALPN: server accepted h2
- Server certificate:
- subject: CN=capzlog.aero
- start date: Dec 31 10:14:59 2024 GMT
- expire date: Mar 31 10:14:58 2025 GMT
- subjectAltName: host "capzlog.aero" matched cert's "capzlog.aero"
- issuer: C=US; O=Let's Encrypt; CN=R10
- SSL certificate verify ok.
- Certificate level 0: Public key type RSA (3072/128 Bits/secBits), signed using sha256WithRSAEncryption
- Certificate level 1: Public key type RSA (2048/112 Bits/secBits), signed using sha256WithRSAEncryption
- Certificate level 2: Public key type RSA (4096/152 Bits/secBits), signed using sha256WithRSAEncryption
- using HTTP/2
- [HTTP/2] [1] OPENED stream for https://capzlog.aero/api/pel/public/externalsystemflights/GetMissingIDs
- [HTTP/2] [1] [:method: OPTIONS]
- [HTTP/2] [1] [:scheme: https]
- [HTTP/2] [1] [:authority: capzlog.aero]
- [HTTP/2] [1] [:path: /api/pel/public/externalsystemflights/GetMissingIDs]
- [HTTP/2] [1] [user-agent: curl/8.6.0]
- [HTTP/2] [1] [accept: */*]
- [HTTP/2] [1] [access-control-request-method: POST]
- [HTTP/2] [1] [origin: https://projectz.numericalsolutions.ch]
> OPTIONS /api/pel/public/externalsystemflights/GetMissingIDs HTTP/2 > Host: capzlog.aero > User-Agent: curl/8.6.0 > Accept: */* > Access-Control-Request-Method: POST > Origin: https://projectz.numericalsolutions.ch > < HTTP/2 204 < cache-control: private < server: Microsoft-IIS/10.0 < access-control-allow-origin: https://projectz.numericalsolutions.ch < access-control-allow-credentials: true < x-aspnet-version: 4.0.30319 < x-powered-by: ASP.NET < date: Thu, 16 Jan 2025 07:12:32 GMT <
- HTTP/2 stream 1 was not closed cleanly: HTTP_1_1_REQUIRED (err 13)
- Downgrades to HTTP/1.1
- Connection #0 to host capzlog.aero left intact
- Issue another request to this URL: 'https://capzlog.aero/api/pel/public/externalsystemflights/GetMissingIDs'
- Found bundle for host: 0x55ecfa0a46e0 [can multiplex]
- Hostname capzlog.aero was found in DNS cache
- Trying 156.67.9.80:443...
- Connected to capzlog.aero (156.67.9.80) port 443
- ALPN: curl offers http/1.1
- SSL reusing session ID
- TLSv1.3 (OUT), TLS handshake, Client hello (1):
- TLSv1.3 (IN), TLS handshake, Server hello (2):
- TLSv1.2 (IN), TLS handshake, Finished (20):
- TLSv1.2 (OUT), TLS change cipher, Change cipher spec (1):
- TLSv1.2 (OUT), TLS handshake, Finished (20):
- SSL connection using TLSv1.2 / ECDHE-RSA-AES256-GCM-SHA384 / secp384r1 / UNDEF
- ALPN: server accepted http/1.1
- Server certificate:
- subject: CN=capzlog.aero
- start date: Dec 31 10:14:59 2024 GMT
- expire date: Mar 31 10:14:58 2025 GMT
- subjectAltName: host "capzlog.aero" matched cert's "capzlog.aero"
- issuer: C=US; O=Let's Encrypt; CN=R10
- SSL certificate verify ok.
- using HTTP/1.x
> OPTIONS /api/pel/public/externalsystemflights/GetMissingIDs HTTP/1.1 > Host: capzlog.aero > User-Agent: curl/8.6.0 > Accept: */* > Access-Control-Request-Method: POST > Origin: https://projectz.numericalsolutions.ch > < HTTP/1.1 204 No Content < Cache-Control: private < Transfer-Encoding: chunked < Server: Microsoft-IIS/10.0 < Access-Control-Allow-Origin: https://projectz.numericalsolutions.ch < Access-Control-Allow-Credentials: true < X-AspNet-Version: 4.0.30319 < X-Powered-By: ASP.NET < Date: Thu, 16 Jan 2025 07:12:32 GMT <
- Connection #1 to host capzlog.aero left intact
Here, a comparison of the "OPTIONS"-HTTP-request as sent by Chrome and by Firefox:
CHROME OPTIONS /api/pel/public/externalsystemflights/GetMissingIDs HTTP/1.1 Accept: */* Accept-Encoding: gzip, deflate, br, zstd Accept-Language: en-US,en;q=0.9a comparison of the "OPTIONS"-HTTP-request as sent by Chrome and by Firefox: Access-Control-Request-Headers: authorization,content-type Access-Control-Request-Method: POST Connection: keep-alive Host: capzlog.aero Origin: https://projectz.numericalsolutions.ch Referer: https://projectz.numericalsolutions.ch/ Sec-Fetch-Dest: empty Sec-Fetch-Mode: cors Sec-Fetch-Site: cross-site User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/132.0.0.0 Safari/537.36
FIREFOX
OPTIONS /api/pel/public/externalsystemflights/GetMissingIDs undefined
Host: capzlog.aero
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:134.0) Gecko/20100101 Firefox/134.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br, zstd
Access-Control-Request-Method: POST
Access-Control-Request-Headers: authorization,content-type
Referer: https://projectz.numericalsolutions.ch/
Origin: https://projectz.numericalsolutions.ch
Connection: keep-alive
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: cross-site
Priority: u=4
TE: trailers
And the response header as seen by Chrome:
CHROME HTTP/1.1 200 OK Content-Type: application/json; charset=utf-8 Content-Language: en Server: Microsoft-IIS/10.0 Access-Control-Allow-Origin: https://projectz.numericalsolutions.ch Access-Control-Allow-Credentials: true Set-Cookie: AppSettings=Culture=en-US&Language=English&CountryAlpha2=CH; expires=Fri, 31-Dec-9999 23:59:59 GMT; path=/; secure; SameSite=Lax X-Powered-By: ASP.NET Date: Thu, 16 Jan 2025 07:19:59 GMT Content-Length: 2
Here, a comparison of the Network Traffic as seen for Chrome and for Firefox:
CHROME 17:07:46.550256 IP ANYPC.57562 > 156.67.9.80.https: Flags [P.], seq 1480736564:1480737180, ack 2430285572, win 501, length 616 17:07:46.557654 IP 156.67.9.80.https > ANYPC.57562: Flags [P.], seq 1:393, ack 616, win 8212, length 392 17:07:46.557654 IP 156.67.9.80.https > ANYPC.57562: Flags [P.], seq 393:427, ack 616, win 8212, length 34 17:07:46.557683 IP ANYPC.57562 > 156.67.9.80.https: Flags [.], ack 393, win 501, length 0 17:07:46.557688 IP ANYPC.57562 > 156.67.9.80.https: Flags [.], ack 427, win 501, length 0 17:07:46.558334 IP ANYPC.57562 > 156.67.9.80.https: Flags [F.], seq 616, ack 427, win 501, length 0 17:07:46.558741 IP ANYPC.42786 > 156.67.9.80.https: Flags [S], seq 2926210792, win 64240, options [mss 1460,sackOK,TS val 2936933242 ecr 0,nop,wscale 7], length 0 17:07:46.562927 IP 156.67.9.80.https > ANYPC.57562: Flags [F.], seq 427, ack 617, win 8212, length 0 17:07:46.562962 IP ANYPC.57562 > 156.67.9.80.https: Flags [.], ack 428, win 501, length 0 17:07:46.563492 IP 156.67.9.80.https > ANYPC.42786: Flags [S.], seq 1974100572, ack 2926210793, win 65535, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0 17:07:46.563514 IP ANYPC.42786 > 156.67.9.80.https: Flags [.], ack 1, win 502, length 0 17:07:46.565558 IP ANYPC.42786 > 156.67.9.80.https: Flags [P.], seq 1:1743, ack 1, win 502, length 1742 17:07:46.572094 IP 156.67.9.80.https > ANYPC.42786: Flags [.], ack 1743, win 8212, length 0 17:07:46.572094 IP 156.67.9.80.https > ANYPC.42786: Flags [P.], seq 1:161, ack 1743, win 8212, length 160 17:07:46.572133 IP ANYPC.42786 > 156.67.9.80.https: Flags [.], ack 161, win 501, length 0 17:07:46.572276 IP ANYPC.42786 > 156.67.9.80.https: Flags [P.], seq 1743:1794, ack 161, win 501, length 51 17:07:46.572421 IP ANYPC.42786 > 156.67.9.80.https: Flags [P.], seq 1794:3197, ack 161, win 501, length 1403 17:07:46.583942 IP 156.67.9.80.https > ANYPC.42786: Flags [.], ack 3197, win 8206, length 0 17:07:46.710020 IP 156.67.9.80.https > ANYPC.42786: Flags [P.], seq 161:638, ack 3197, win 8206, length 477 17:07:46.751327 IP ANYPC.42786 > 156.67.9.80.https: Flags [.], ack 638, win 501, length 0 17:07:46.754201 IP 156.67.9.80.https > ANYPC.42786: Flags [P.], seq 161:638, ack 3197, win 8206, length 477 17:07:46.754231 IP ANYPC.42786 > 156.67.9.80.https: Flags [.], ack 638, win 501, options [nop,nop,sack 1 {161:638}], length 0$
FIREFOX 17:08:28.962851 IP ANYPC.35980 > 156.67.9.80.https: Flags [S], seq 2319755284, win 64240, options [mss 1460,sackOK,TS val 2936975646 ecr 0,nop,wscale 7], length 0 17:08:28.972248 IP 156.67.9.80.https > ANYPC.35980: Flags [S.], seq 1053801102, ack 2319755285, win 65535, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0 17:08:28.972330 IP ANYPC.35980 > 156.67.9.80.https: Flags [.], ack 1, win 502, length 0 17:08:28.974266 IP ANYPC.35980 > 156.67.9.80.https: Flags [P.], seq 1:1894, ack 1, win 502, length 1893 17:08:28.987389 IP 156.67.9.80.https > ANYPC.35980: Flags [.], ack 1894, win 1026, length 0 17:08:28.987433 IP 156.67.9.80.https > ANYPC.35980: Flags [P.], seq 2921:3937, ack 1894, win 1026, length 1016 17:08:28.987461 IP ANYPC.35980 > 156.67.9.80.https: Flags [.], ack 1, win 502, options [nop,nop,sack 1 {2921:3937}], length 0 17:08:28.987598 IP 156.67.9.80.https > ANYPC.35980: Flags [.], seq 1:1461, ack 1894, win 1026, length 1460 17:08:28.987647 IP ANYPC.35980 > 156.67.9.80.https: Flags [.], ack 1461, win 524, options [nop,nop,sack 1 {2921:3937}], length 0 17:08:28.987682 IP 156.67.9.80.https > ANYPC.35980: Flags [.], seq 1461:2921, ack 1894, win 1026, length 1460 17:08:28.987707 IP ANYPC.35980 > 156.67.9.80.https: Flags [.], ack 3937, win 547, length 0 17:08:28.994553 IP ANYPC.35980 > 156.67.9.80.https: Flags [P.], seq 1894:2052, ack 3937, win 547, length 158 17:08:29.005007 IP 156.67.9.80.https > ANYPC.35980: Flags [P.], seq 3937:3988, ack 2052, win 1025, length 51 17:08:29.005007 IP 156.67.9.80.https > ANYPC.35980: Flags [P.], seq 3988:4057, ack 2052, win 1025, length 69 17:08:29.005700 IP ANYPC.35980 > 156.67.9.80.https: Flags [.], ack 4057, win 547, length 0 17:08:29.006086 IP ANYPC.35980 > 156.67.9.80.https: Flags [P.], seq 2052:2151, ack 4057, win 547, length 99 17:08:29.006123 IP ANYPC.35980 > 156.67.9.80.https: Flags [P.], seq 2151:2577, ack 4057, win 547, length 426 17:08:29.008948 IP ANYPC.35980 > 156.67.9.80.https: Flags [P.], seq 2577:2615, ack 4057, win 547, length 38 17:08:29.018116 IP 156.67.9.80.https > ANYPC.35980: Flags [.], ack 2615, win 1023, length 0 17:08:29.018116 IP 156.67.9.80.https > ANYPC.35980: Flags [P.], seq 4057:4095, ack 2615, win 1023, length 38 17:08:29.024518 IP 156.67.9.80.https > ANYPC.35980: Flags [P.], seq 4095:4322, ack 2615, win 1023, length 227 17:08:29.024518 IP 156.67.9.80.https > ANYPC.35980: Flags [P.], seq 4322:4364, ack 2615, win 1023, length 42 17:08:29.024943 IP ANYPC.35980 > 156.67.9.80.https: Flags [.], ack 4364, win 570, length 0 17:08:35.342337 IP ANYPC.42786 > 156.67.9.80.https: Flags [.], ack 1974101210, win 501, length 0 17:08:35.349317 IP 156.67.9.80.https > ANYPC.42786: Flags [.], ack 1, win 8206, length 0
I really do not know what to do anymore to solve that problem.
As the problem is impacting hundreds of users, I really hope there is a solution.
In advance thanks for your help.
Chosen solution
I notice CURL had to fall back to HTTP/1.1:
- HTTP/2 stream 1 was not closed cleanly: HTTP_1_1_REQUIRED (err 13)
- Downgrades to HTTP/1.1
Similarly, Chrome used HTTP/1.1.
I can't tell from your screenshots whether Firefox connected (or tried connecting) with HTTP/1.1. Maybe the "not closed cleanly" could be causing the failure in Firefox here? As a test, you could disable HTTP/2 in Firefox -- here's how:
(1) In a new tab, type or paste about:config in the address bar and press Enter/Return. Click the button accepting the risk.
More info on about:config: Configuration Editor for Firefox. The moderators would like us to remind you that changes made through this back door aren't fully supported and aren't guaranteed to continue working in the future.
(2) In the search box in the page, type or paste network.http.http2 and pause while the list is filtered. Firefox should list a large number of parameters.
(3) Double-click the network.http.http2.enabled preference to switch the value from true to false
Any difference? (Please note that this is only for testing and some sites might require HTTP/2.)
Read this answer in context 👍 2All Replies (2)
Did you ask that site to verify if it works Firefox?
Chosen Solution
I notice CURL had to fall back to HTTP/1.1:
- HTTP/2 stream 1 was not closed cleanly: HTTP_1_1_REQUIRED (err 13)
- Downgrades to HTTP/1.1
Similarly, Chrome used HTTP/1.1.
I can't tell from your screenshots whether Firefox connected (or tried connecting) with HTTP/1.1. Maybe the "not closed cleanly" could be causing the failure in Firefox here? As a test, you could disable HTTP/2 in Firefox -- here's how:
(1) In a new tab, type or paste about:config in the address bar and press Enter/Return. Click the button accepting the risk.
More info on about:config: Configuration Editor for Firefox. The moderators would like us to remind you that changes made through this back door aren't fully supported and aren't guaranteed to continue working in the future.
(2) In the search box in the page, type or paste network.http.http2 and pause while the list is filtered. Firefox should list a large number of parameters.
(3) Double-click the network.http.http2.enabled preference to switch the value from true to false
Any difference? (Please note that this is only for testing and some sites might require HTTP/2.)