can't deploy private CA with GPO
Hi all
I'm trying to deploy my public CA to my Firefox on Windows enviroment. We need because I have set up a SSL inspection that resign public certs of websites in order to perform inspection.
The CA cert is deployed through a GPO to every computer's store, and then, a policy from custom Firefox ESR admx's is telling clients to use Windows certificate store. But no way is working. I can't see the cert imported.
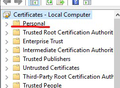
My public CA cert is deployed in the store, inside the folders you can see in the screen and i checked every computer had received it correctly.
Please help!! Thanks
すべての返信 (18)
Hello Dark345,
You posted this 5 days ago and haven't received any response yet (sorry .... )
I am a complete layman in this area, but my posting here just might promp the experts to come up with a perfect solution for you .....
In the mean time : this article is all I could find, and may not even come close to what you are looking for :
unfortunately modifying security.enterprise_roots.enabled to TRUE is a legacy solution, it seems. Now with new Firefox ESR 60.X it can be deployed using Windows GPO.
Infact, setting the GPO to enabled, as I did, it triggers security.enterprise_roots.enabled to be TRUE and locked. But my certificates aren't imported.
So a couple things could be going on here.
1. We weren't reading intermediate certificates from the Windows store (this has been fixed).
2. It could be a client certificate?
Could you try a currently nightly Firefox build and see if it's still a a problem? If so, we might want to look at the cert.
Thanks.
See also:
Maybe also check the Browser Console for related message (don't know whether GPO errors show in this console).
what do you mean by: 2. It could be a client certificate?
Do I have to import certificates in Computer's o User's store?
For the moment I'm off, I will try to log something in next weekend
> what do you mean by: 2. It could be a client certificate?
It's probably not if you don't know what I meant :)
> Do I have to import certificates in Computer's o User's store?
Yes, and it sounds like you already have. The certificates from the OS will not show up in Firefox, they will just work.
Yes, and it sounds like you already have. The certificates from the OS will not show up in Firefox, they will just work. </blockquote>
No, I mean, do Firefox read from User OR Computer store? Or both? Windows has two stores.
> No, I mean, do Firefox read from User OR Computer store? Or both? Windows has two stores.
It should read from both. But you won't see them in Firefox settings.
Maybe I figured it out... I placed my (intermediate) root CA public cert into the Computer's Personal Store, and now it seems to work..
Am I right to assume Firefox reads from the Personal store only, and not from the others ?
We only read added certs, not built in certs, yes.
But it should read from the computer store.
it's working on a W10 workstation, but on W7 clients not working, no matter where I put my certs
What does about:policies show on your Windows 7 machines?
It says it can't display the page
about:policies requires Firefox 63 or later, so if these devices use Firefox 60 ESR then about:policies isn't available. This only leaves the Browser Console and the about:config to check the state of security.enterprise_roots.enabled and possibly the Certificate Manager.
I tried both, no luck in finding some logs concerning the enforced policy..
Dark345: So where are you with things right now? What's still not working?
still no luck. GPO is active, w7 clients refused to load from windows computer store, I tried everything. i will try to load from a file instead.
That's really odd. I'm betting it's related to intermediate certs. Would you consider opening a bugzilla bug so we could debug? We can provide instructions on how to log.
https://developer.mozilla.org/en-US/docs/Mozilla/Developer_guide/Gecko_Logging
set MOZ_LOG=pipnss:4,certverifier:4 set MOZ_LOG_FILE="c:\logs\log.txt"
See: