downloaded firefox-patch.js what should I do
I got a notice to patch firefox on a new site. Downloaded and clicked on it without thinking. Looks like it is a virus or malware. Now I am getting repeated requests from flash for permission to update. What should I do? Thanks
Todas as respostas (14)
hi, that "urgent update" was not genuine but a scam tactic that is trying to trick you into installing malware! only download firefox from its official location at mozilla.org - in addition updates are handled automatically by firefox so you don't have to download anything (you can initiate a check for updates in the firefox menu ≡ > help ? > about firefox).
you should run a full scan of your system with the security software already in place and multiple other tools like the free version of malwarebytes, eset online one-time scanner & adwcleaner in order to try to contain the damage.
Please note that Firefox will never advise users about updates using on any other website besides those owned and operated by Mozilla. The only update notification that you may receive in Firefox may appear in the bottom corner on your browser.
The first thing that you should do is delete the file that you downloaded. Next you should browse your addons that are install on your Firefox and remove any that you believe are illegitimate or that you don't remember installing.
Next, you should scan your system for infection. You can use some of the free tools that are listed in the Troubleshoot Firefox issues caused by malware Mozilla support article.
Also, please ensure that you report this issue to Mozilla, via the fraud reporting page so that they can further investigate the issue and take action against it.
Thanks. Please let us know if you are able to repair this issue.
Please refer to this Mozilla support article for further information on protecting yourself from scams:
Based on what I saw in a previous example, the .js file specifies a site to connect with to download malware. This may be different today than it was yesterday or the day before. However, some analysts have identified the "Kovter" trojan as one of the infections. In case you end up needing it, Symantec (maker of Norton software) has released a special tool: https://www.symantec.com/security_response/writeup.jsp?docid=2015-092321-2230-99
Thanks for the help. I am running the antivirus programs now. I will also check out the "Kovter" trojan. The window just popped up in a article off of the Yahoo news page. I will be much more careful in the future. It looked very much like something from Firefox. Orange page with the logo.
Brick44 said
It looked very much like something from Firefox. Orange page with the logo.
The desktop Firefox updates are done internally in Firefox itself (with a .mar type of file) whether on Windows, Mac OSX or Linux. Mozilla the maker of the Firefox web browser has no reason to host Firefox downloads or updates at random named websites.
The concept of having a random site with a product name, logo and words like security, urgent, update to try and trick people (on Windows) into downloading the file and running it is nothing new.
These scammers were serving a firefox-patch.exe and then more recently been serving the firefox-patch.js files. Even the .exe's according to virustotal scans had recent compilation dates which showed they were trying to get around blocking or flagging before switching to .js.
Thanks again. So far none of the scans have detected anything. It seems unlikely that the machine is not infected. I will keep scanning with the various tools. Is there anything specifically I should be looking for?
Brick44 said
Is there anything specifically I should be looking for?
Hmm, that's a tough one. Someone could analyze the .js file to see exactly what it does, but I don't think you'll find a researcher with a machine they are willing to infect on this forum...
I'll do it. I've got a system at home that I use solely for infecting.
I will send you a private message with my email address and if you just compress the Javascript file into a ZIP file and email it to me, I will see if I can take a look at it.
Wesley Branton said
I'll do it. I've got a system at home that I use solely for infecting.
This is why I don't buy used computers. ;-)
jscher2000 said
This is why I don't buy used computers. ;-)
Normally I would not buy a used one either because of not knowing history or hardware issues. I got lucky in getting a very clean lightly used Lenovo m91p with 4GB Ram, 500GB HDD and i5-2400 for only $25 a while back. It did have Win7 Pro on it but was sabotaged in such a way it could not really be booted. I just put Linux on it anyways to use as a backup PC.
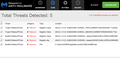
Well Malwarebytes did find something after Mcafee and eset came up empty. 2 Trojans fileless.mtgen 3 Rootkit.filess.mtgen I will hope that helps somebody.
I will also try the kevter removal tool and the adware program and let you know what it comes up with.
I ran both tools and both came up clean. Is there anything else I should do to protect myself? I do run Mcafee firewall and antivirus, but as I said it did not detect anything. Thanks again for all the help
It sounds like Malwarebytes was the best tool to uncover the registry-based (file-less) infection I've seen mentioned in articles. Hopefully that is the end of it.
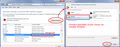
One thing you could consider for the future is to prevent Windows from running .js files as administrative scripts, and instead just display their contents in a text editor when opened.
The exact method for this depends on your version of Windows, but all recent versions should have a control panel where you can specify the program you want to open different kinds of files by their file extension. I have attached a screen shot from Windows 7, for example.
The following article has a thorough explanation and lots of screen shots. Note: If you don't have a .js file available to right-click, you may need to create one to follow its steps. http://www.computerworld.com/article/3090146/windows-pcs/blocking-javascript-can-stop-some-windows-malware.html